The indaHash ICO was a great success, and unfortunately almost every such kind of success is accompanied by scammers who want to earn on it. The same was with the indaHash Coin distribution event. As our project grew and the number of participants in the distribution event rose, the number of scam websites, fake social media accounts and telegram scammers also grew. But, we have not been idle under such circumstances. We fought with all those malicious attempts to steal our contributors’ ETH both during and after the indaHash Coin distribution event. This article has been prepared by our legal team to warn other projects how scammers are acting and to demonstrate some techniques on how we fought with them effectively.
1. Malicious websites
Malicious websites (l(L)ndahash.com etc.) were broadly used during the indaHash Coin distribution event, along with many other types of spam which were aimed at guiding participants to these websites. Most of them contained a QR code or wallet address which was owned by scammers instead of indaHash. For the sake of participants we were constantly monitoring the web in order to find and block them all. We also sent a mailing warning against such scams. Homepages of malicious websites often (more or less precisely) resembled indaHash’s subpage dedicated to the ICO. Sometimes it was nearly impossible to determine whether it was the original or not without looking carefully at the web address. The only thing which was always different was the ethereum wallet address :). The addresses of malicious websites were similar to the indaHash website; they usually differed in the domain or letters in the name e.g. indahash.cc and indaHaśh.com.
Over the last months we have blocked over a dozen of them. How did we do it? The first step is to determine the host of the malicious website. There is a wide range of services that can help you with this, such as:
It’s important to check the hosting provider on different websites because results can be different. Also remember to check nameservers, as they can lead you to the correct hosting provider.
After determining the hosting company, you should send them an email in order to report the abuse. Often sending emails to the support does not provide the expected outcome. Most hosting providers have a special email used specifically for abuse complains which may look like the following: abuse@hostingprovider.com. You should look for that. Since these addresses are sometimes not very visible on the website, it might be wise to use a search engine by typing e.g. name of hosting provider+abuse+report. If you can’t find the designated email address, and there is no response from the support email address, the best way of establishing a correct email address is calling support.
Sometimes a website is protected by Cloudflare, which is very helpful when it comes to abuses. All you need to do is to fill out the abuse form which can be found here: http://cloudflare.com/abuse/form. Bear in mind that not every hosting provider is interested in blocking malicious websites. Sometimes there is no response to the violation report and some of them want a cryptocurrency or other payment in exchange for taking down a scammer’s website(s).
In case it’s impossible to block the malicious website through the hosting provider you should try to contact the domain registrar company. You can check it through this link: https://www.mydomain.com/whois/whois.bml. After determining the domain registrar company, as in the case with hosting providers, you should send them an email in order to report the abuse.
In addition to the above-mentioned solutions, you should always report an abuse to Google in order to prevent malicious websites from being shown in Google search results. The following links may be useful for such reporting:
- https://support.google.com/legal/contact/lr_dmca?product=groups&uraw=&hl=en
- https://safebrowsing.google.com/safebrowsing/report_phish/?hl=en
- https://safebrowsing.google.com/safebrowsing/report_badware/
Sometimes scammers use Google Adwords to promote their sites. In that case, aside from above, use the following link:
https://support.google.com/adwords/troubleshooter/4578507.
2. Malicious Twitter accounts
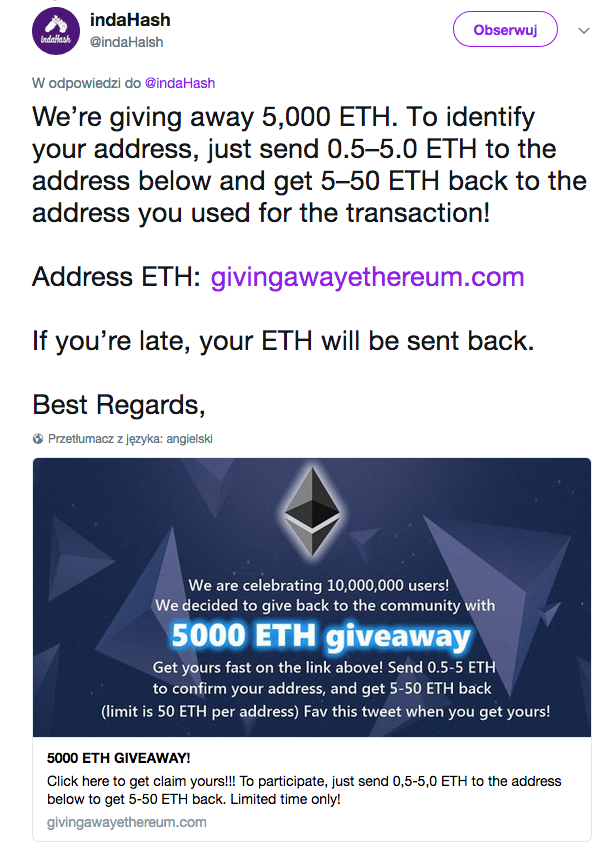
The last few months have shown us that each day scammers are getting more and more creativite. They try to create as credible social media profiles as it is possible. The scammers do so, and there is a trend of making promises of sending a higher value of a cryptocurrency to those who initially are told to send a cryptocurrency to the scammer. Often times fake discounts/bonuses are offered for participating in an ICO. It is only safe to simply avoid any such transactions and participate only via an official website.
(Fake indaHash profile. In this example the scammer has added an “l” to his Twitter nickname)
Using well-known authorities as well as human inattention, they do simply steal money.
In order to get a malicious Twitter account deleted you need to go deeper than casual clicking on report.
When an account is using your logo you can report a copyright infringement:
https://help.twitter.com/forms/dmca
or a trademark issue:
https://help.twitter.com/forms/trademark
or impersonation:
https://help.twitter.com/forms/impersonation
or counterfeit goods:
https://help.twitter.com/forms/counterfeit
3. Malicious Facebook accounts
With Facebook we have noticed the same trends as with Twitter, but on a smaller scale. Scammers may give false information regarding participation in an ICO, and often times create a fake page mimicking the one of a real company conducting an ICO.
Facebook is also similar to Twitter when it comes to the “report abuse” button; it won’t do much and the whole procedure will take a long time.
If you need to act fast you should report a violation or infringement of your rights!
It can be done here:
https://www.facebook.com/help/contact/634636770043106?helpref=faq_content
4. Malicious YouTube videos
It is often the case that YouTubers will repost an official video, and then in the video description they may describe a way to participate in an ICO that contains false information (such as an incorrect Smart Contract Address). Many times you can find scammers in comments offering fake discounts/bonuses just as you can find on Facebook and Twitter.
When you want to report a malicious YouTube video you should use the report button on the bottom right side of the video, or you can go straight to this link:
https://www.youtube.com/copyright_complaint_form
5. Telegram scammers
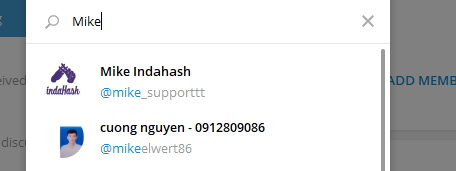
During the indaHash Coin distribution event admins had to ban fake accounts on a daily basis. The most predominant way scammers would try to trick chat users into sending them cryptocurrency is to copy the name and photo of an admin (on Telegram any new user can have any nickname; even existing ones) and send a direct message to chat users offering a larger discount/bonus than is given by the real company conducting an ICO. Most official channels warn users of the possibility of scammers and state not to ask questions in a direct message and/or believe anything they are told in a direct message as official information is only given my admins in the chat.
When it comes to Telegram scammers the best way to report them, aside from clicking report in the app, is to write an email to the following address: abuse@telegram.org You can also let the chat admins know when you are suspicious of a scammer.
Note: If you let the admins know in the main chat, the scammers can sometimes change their names before the admins can ban them from the chat. As a rule of thumb, most Telegram chats mention that admins will never ask you for any transactions in a private message. The most important thing here is to build awareness among the social communities and to teach them how to avoid such contacts.
(Scammer acting as indaHash Telegram administrator)
6. Malicious Emails
It is a well-know fact, that phishing email messages are one of the most common attacks on users. With the usage of addresses registered on almost identically looking domains, scammers are masquerading as well-known and trusted companies and brands. Due to a lack of attention it is possible to become one of their victims.
It is especially important to carefully analyze a sender’s details ( FROM field ) when it comes to emails regarding the topic of cryptocurrencies and ICOs.
During the process of conducting the ICO of indaHash Coin, we saw plenty of malicious activities having an aim of stealing money from other people. Some of their messages were almost identical to ours: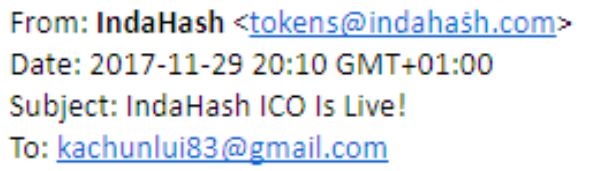
Even right now the difference is barely visible. In the mentioned example, a scammer, in order to get trust, replaced the letter “s” with “ś”, pretending to look the same as “tokens@indahash.com”.
Each time you receive an official message, always try to determine its source.
Best regards,
indaHash Legal Team 🙂